
Resetting the root password is the most easiest tasks in Linux. You can read the article Reset Root Password in Linux to know how to do this. To plug this security hole and to make Linux more secure with set a password for editing the boot parameters. This password will make sure only users knowing this have access to edit the boot parameters. There are two ways of doing this. If you have GUI installed it is very easy to accomplish this task. For command-line installations you have to be extra careful not to edit anything else when executing commands like sed.
Step 1: Generate a MD5 encrypted password using grub-md5-crypt
Using the grub-md5-crypt command an encrypted password should be created. I’ve outlined two methods for users with GUI installed and command-line only users.
For GUI users
Open a terminal from your desktop and type
grub-md5-crypt
you’ll be prompted twice to enter a password and then a MD5 encrypted password will be shown. Copy this password and move on to the next step.
For command-line users
From the command line you can execute the same command but how can the generated password be copied ? For this we need to get a plaintext password from a file, pass the contents as an input to grub-md5-crypt and save the output in that file again. Execute the following commands
touch tempfile
vi tempfile
Type the desired password in the first line and in the next line too type the same password, save the file and exit. We’ll be passing these as the input for grub-md5-encrypt. In case you’re wondering whether you can use echo to write the password to this file don’t do it because the plaintext password will show up in history. Now execute the following command.
echo $(cat tempfile | grub-md5-encrypt 2> /dev/null) > tempfile
This command will pass the contents of tempfile to grub-md5-encrypt any STDERRs will be suppressed by /dev/null and the entire output of this will be echoed back to tempfile. Now open tempfile you’ll find the following contents
Password: Retype password: your-encrypted-password
Edit the file to look as following
password --md5 your-encrypted-password
make sure you don’t accidentally edit the encrypted password string. Now move on to the next step.
Step 2: Add the password to /boot/grub/grub.conf
Before proceeding with this step you MUST backup the /boot/grub/grub.conf file because you are bound to make a lot of errors in this step. The following command will create a copy of the file at /boot/grub/grub.conf.bak
cp /boot/grub/grub.conf{,.bak}
If you’ve been doing the GUI method just open /boot/grub/grub.conf file and add the following line at the beginning of the file
password --md5 encrypted-password
The encrypted-password is the string you copied after executing the grub-md5-crypt command.
For command-line warriors, using the sed command add the password to the grub.conf. Please make sure you have a backup copy.
sed "1 a $(cat tempfile)" /boot/grub/grub.conf > tempfile
mv tempfile /boot/grub/grub.conf
When prompted to overwrite enter y to confirm. The first command adds the password option to the first line and writes the entire contents of grub.conf to tempfile Now is the time to check whether anything else have been modified in the grub.conf file.
diff /boot/grub/grub.conf{,.bak}
The original file and backup copy are checked for differences. You should only see password –md5 <md5-password> if something else differs review the contents and make necessary changes. Now reboot your system and see it in action.
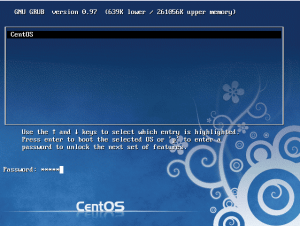
Press p enter the correct password now you can edit the kernel arguments and other boot options. The reason why we are using only one tempfile to store passwords and process things is that to add more security. After storing the plaintext password when you echo the encrypted password the > symbol is used instead of >> so that the plaintext password is overwritten. Finally the mv command is used so the the tempfile is moved and erased. Our aim is to store the encrypted password only in the grub.conf file and no where else.




Leave a Reply