This is a tutorial to configure Apache Web Server Load Balancing in Linux using the mod_proxy_balancer module. So additional software isn’t required. This tutorial is written for Linux but this can also be applied to windows systems running Apache. This setup makes use of four computers. The first computer is the proxy load balancer, the second and third computers are the normal web servers which will respond to the requests and the fourth computer hosts the web content that is to be served by the web servers. The reason for separating the content is to make sure the same content is served by both the web servers. The fourth computer is optional, you can use tools like rsync to keep the content of both web servers synchronized, but that add up to network traffic. The number of web servers can be increased as per requirement.Continue Reading…
How to set a GRUB password
Resetting the root password is the most easiest tasks in Linux. You can read the article Reset Root Password in Linux to know how to do this. To plug this security hole and to make Linux more secure with set a password for editing the boot parameters. This password will make sure only users knowing this have access to edit the boot parameters. There are two ways of doing this. If you have GUI installed it is very easy to accomplish this task. For command-line installations you have to be extra careful not to edit anything else when executing commands like sed.Continue Reading…
Linux password lockout policy
Linux password lockout policy can be configured using PAM (Pluggable Authentication Modules) to lock a user’s account temporarily if they attempt to bruteforce into an account by trying various password combinations. This configuration uses the pam_tally2.so module. Bruteforce hacking is a method to find a user’s password by trying to login with various password combinations. By having a password lockout policy such users can be locked out of their account if a certain number of incorrect passwords are entered. While trying this tutorial in your system make sure you have the file /lib/security/pam_tally2.so if it isn’t there trying this out will lock all user accounts even if you enter the correct password.Continue Reading…
How to create a swap file in Linux
A swap file can be created while installing Linux operating system, if you forgot to do so you can read this tutorial and create one after installation. Even if you need additional swap memory this tutorial will be useful. I’ve only explained the command line way of creating a swap file which most administrators will use, its upto you to explore the GUI technique. For executing the commands in this tutorial you need to have root access or atleast sudo permissions for these commands and permissions to edit the fstab file.Continue Reading…
How to Change SELinux modes
The SELinux (Security Enhanced Linux) is a feature of Linux operating systems which bullet poofs your system against security holes even if you accidentally chmod a file or directory to 777. It uses file contexts to find which files belongs to what type. SELinux operates in many different modes and this article I’ll show you how to switch between these modes temporarily or permanently. I’ll also show you how to disable selinux completely, but be warned do not do this unless you know what you’re doing.Continue Reading…
Change Linux Login banner
Banner screens provide a lot of important and warm welcome messages, but they also expose the system to a number of threats by displaying the exact version number. In Linux by default after your system starts when you come to the terminal you may see a screen like this
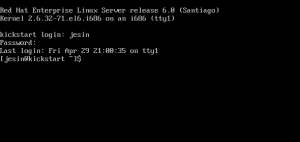
You can customize this banner according to your liking to add a personalized message or to make it more informative.Continue Reading…
- « Previous Page
- 1
- …
- 12
- 13
- 14
- 15
- 16
- …
- 25
- Next Page »



